Tag Archives for " php "
PHP: Top command-line options
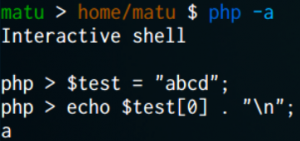
Here are some useful php command line options that you will love. Ever wanted to test a quick snippet of code without having to save it to a file and then run it? Well check this out! If you invoke php with the -a flag it will drop you into an interactive session. This is nothing more than a REPL (Read, Eval, Print, Loop) that let’s you type any php code and execute it immediately. It also helps you with tab-completion of variable names and functions.
You could even use include to load a php file and test functions in isolation, so this is useful in case you don’t have unit test and want to make sure that a function is doing what it’s supposed to or if this function would usually be triggered by something like an ajax call but you don’t have that available yet.
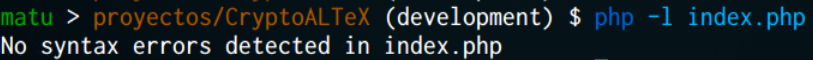
If you are using a text editor instead of a full blown php IDE you will like the next option: php -l will perfom a syntax check on your code without actually running it.
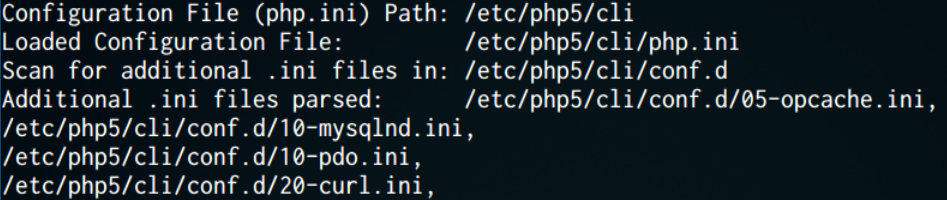
Another useful one is php –ini which will show you what configuration files are being loaded by php (for the CLI version), this information is also available via the phpinfo() function.
And finally another option you may find useful is: php -S localhost:80 which spins up a dev web server. This is similar to the python version python -m SimpleHTTPServer
Make sure you try those out and let me know in the comments if you know any other cool php tricks 
Related posts:
http://www.blackbytes.info/2012/09/php-arrays/
PHP Arrays
This is an introduction to PHP arrays, so if you are new to the language or you just need a refresher you can get up to speed pretty fast.
This is how we initialize an empty array and add some elements to it:
|
1 2 |
$chars = array(); array_push($chars,'a','b','c'); |
Then we can see it’s contents using the print_r() function. You may want to put this between <pre> tags for better formatting.
Continue reading
Analysis of a backdoored Web shell
I frequent the elearnsecurity student forums, an one of the common questions is about webshells and it ends up with a link to backdoored scripts. Here is my quick analysis of one of them.
I start downloading our target and open it with a text editor, and what I see is immediately suspicious: the code is all packed on one line and what seems to be base64 encoding, scrolling all the way to the end confirms this:
Time to reach for some base64 tool. In this case I used:
http://www.opinionatedgeek.com/dotnet/tools/base64decode/
Clicking on “Decode safely as text” will get us the decoded script. Now I paste this into my text editor for syntax highlighting and skimmed over the code to see if something stood out. First thing I noticed is it seemed that no further obfuscation has been done in this code other than a few blobs of base64 that seem to be some images and a bind shell script in perl. By the end of the file something got my attention; a script tag loading some js code from the site this was downloaded from.
A wget later we get this:
Well, looks like we found what we where looking for! This is loaded when you use the shell. And what it does is create an invisible image that request a script from the malicious domain sending our current url, this means that these guys are getting reported of websites that have been compromised using their shell so they can use it to get access and do whatever they please without any effort. I think I don’t need to tell you how bad this would be if this happens to be a pentesting client.